Introduction
As a Storage Administrator we are always involved in storage migrations to new hardware. They are time consuming and depending on the migration type can be difficult. EMC offers several licensed tools that can help alleviate and automate part of this process. One such tool is OpenReplicator, which we cover how to use this array based migration tool while migrating from a VMAX 40k to XtremIO system over IVR/ISL using a hot push operation.
Note: If you are using RecoverPoint and the LUNs have a Device Tag of RecoverPoint you will have to stop replication and remove the Device Tag from the LUN’s as the hot push will fail.
Getting Setup
There are several steps needed to setup arrays for migration.
- Zoning VMAX initiators to XtremIO Initators
- Zoning for new host initiators for new storage
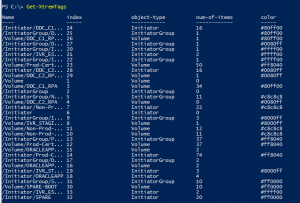
- Register VMAX initiators in XtremIO
- Create new volumes on XtremIO
- Map VMAX initiators to new volumes
- Create volume pairing text file for OpenReplicator
So with that we need to start getting preparations started.
Step 1 – Create IVR Zoning for VMAX to XIO X1 & X2 following your standard practice.
Step 2. Verify logins – Find newly logged in XIO Initiators on VMAX
$ symaccess -sid 2256 list logins | grep -i 514f0c5003a7
514f0c5003a76311 Fibre NULL NULL b7b547 Yes Yes
514f0c5003a76315 Fibre NULL NULL b7b546 Yes Yes
514f0c5003a76311 Fibre NULL NULL b7b547 Yes Yes
514f0c5003a76315 Fibre NULL NULL b7b546 Yes Yes
514f0c5003a76300 Fibre NULL NULL 45b533 Yes Yes
514f0c5003a76304 Fibre NULL NULL 45b536 Yes Yes
514f0c5003a76300 Fibre NULL NULL 45b533 Yes Yes
514f0c5003a76304 Fibre NULL NULL 45b536 Yes Yes
Step 3. Discover / Verify logins and remote port wwn from control array:
Note: You must run the commands to cause the VMAX Initiators to login to XtremIO.
$ symsan list -sanluns -wwn 514f0c5003a76300 -sid 2256 -dir 9f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76304 -sid 2256 -dir 9f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76300 -sid 2256 -dir 11f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76304 -sid 2256 -dir 11f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76311 -sid 2256 -dir 6f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76315 -sid 2256 -dir 6f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76311 -sid 2256 -dir 8f -p 0
$ symsan list -sanluns -wwn 514f0c5003a76315 -sid 2256 -dir 8f -p 0
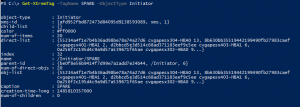
Step 4. Register VMAX Initators on XIO and Register new Host initiators
Login to XIO GUI or web interface and follow standard process to register the VMAX Initiators, tag and color code if you want.
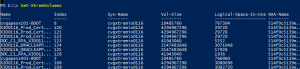
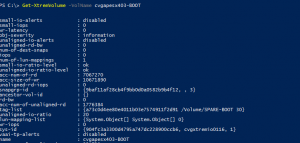
Step 5. Create volumes for server on XIO bigger than original.
Tag volumes to destination server name if you want to, this is optional, but makes it easier to manage and find volumes.
Assign VMAX Initiators to new volumes, this will create the NAA ID. Record the naa id as you will need this information when pairing later.
Step 6. Create cvgwsclu01_pair.txt for migration. This is the file needed for pairing the old to the new. Save the file to a local drive that you will be running commands from, not a mount or mapped drive, it will cause errors.
The format is #Control Device (VMAX) #Remote Device (XIO naa id)
Symdev=000195702256:1887 wwn=514f0c5139e001ae
Symdev=000195702256:1888 wwn=514f0c5139e001ad
Symdev=000195702256:188F wwn=514f0c5139e001ac
Symdev=000195702256:189E wwn=514f0c5139e001ab
At this point we are ready to create the hot push session.
Step 7. Create Open Replicator hot push session on control array VMAX using text file containing device pairing information. We are using the symrcopy command with precopy, push, hot and differential flags.
$ symrcopy create -precopy -name OR_CVGWSCLU01 -push -hot -file cvgwsclu01_pair.txt -differential -frontend_zero
Query open replicator session and verify all device pairs (Control Device and Remote Device) have status of “PreCopy”.
$ symrcopy -f cvgwsclu01_pair.txt query -detail
Continue to query the operation until 100% is showing in the output.
The Flip
We are ready to make the change to the new storage. First step is to shutdown hosts.
Check the FA ports to make sure they are not logged in. The dirports will be different for your application and sid of your VMAX will be different in the examples, change accordingly. The output will show them not logged in.
$ symaccess -sid 2256 list logins -dirport 7f:0
Activate our Open Replicator session.
$ symrcopy activate -file cvgwsclu01_pair.txt -consistent
Check Progress – Check until CTL shows Copied
$ symrcopy query -file cvgwsclu01_pair.txt -detail
Be careful setting pace as it will cause disruptions on VMAX to other datastores / LUNS accessing the VMAX. Avoid pace of 0. Default pace is 5, in this example we are changing to 3.
$ symrcopy -file cvgwsclu01_pair.txt set pace 3
Verify all device pairs are in copied state
$ symrcopy -file cvgwsclu01_pair.txt verify
Now we need to get any changes, so we will run a recreate operation with precopy
$ symrcopy recreate -file cvgwsclu01_pair.txt -precopy
Verify progress to 100% PreCopy.
$ symrcopy query -file cvgwsclu01_pair.txt -detail
Perform final activation using the consistent flag.
$ symrcopy activate -file cvgwsclu01_pair.txt -consistent
Verify all device pairs are in copied state
$ symrcopy -file cvgwsclu01_pair.txt verify
Check status if Copied now terminate the open replicator session, we are done.
$ symrcopy -file cvgwsclu01_pair.txt terminate
Should show no session
$ symrcopy query -file cvgwsclu01_pair.txt -detail
We are now compete with Open Replicator, at this point we need to remove the masking will for the servers on the old storage on the VMAX. Remember to change the name and sid to your environment.
Remove Masking view from VMAX
$ symaccess -sid 2256 delete view -name CVGWSCLU01_CLUSTER_MV
Check device masking assignments – should be empty
$ symaccess -sid 2256 list assignments -dev 1A98
Login to XtremeIO and remove assigned VMAX ports from Volumes and assign servers Initiators to volumes.
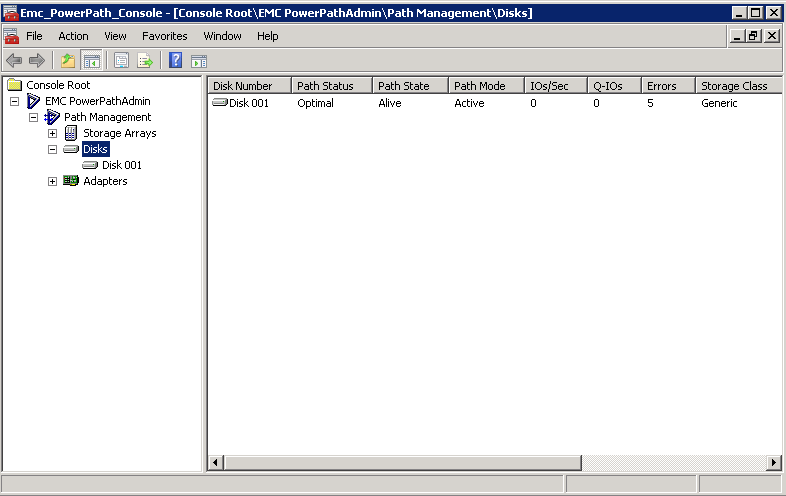
Now we can power up a server or one of the cluster nodes and verify in PowerPath that the server sees XtremIO storage only and drives are online and data in-tact.
Conclusion
As we can see we have effectively performed a OpenReplicator hot push array based migration from VMAX to XtremIO. I hope this adds another tool to your arsenal for managing and migrating data on your EMC storage!